Endpoint security
Configure endpoint security to protect Gradient deployments from unauthorized users.
How endpoint security works
Gradient deployments currently have two levels of endpoint security: public and protected.
Public: Public endpoints are the default status for Gradient deployments if left unspecified. Public endpoints will allow any user with access to the deployment endpoint to access the service. This can be used for internal testing, allowing others easy access to your service, or prototyping.
Protected: Protected endpoints restrict access to the deployment using a basic access authentication encoded token. To access these endpoints, users need to pass in the encoded token in the authorization header with the API request. If no authorization header, or an incorrect token is passed, the user will receive a 401 Unauthorized response.
Endpoint security configuration
If creating a deployment through the console, users can configure endpoint security under Advanced Options. Users can either generate a new secret or use the value of an existing secret as the security token.
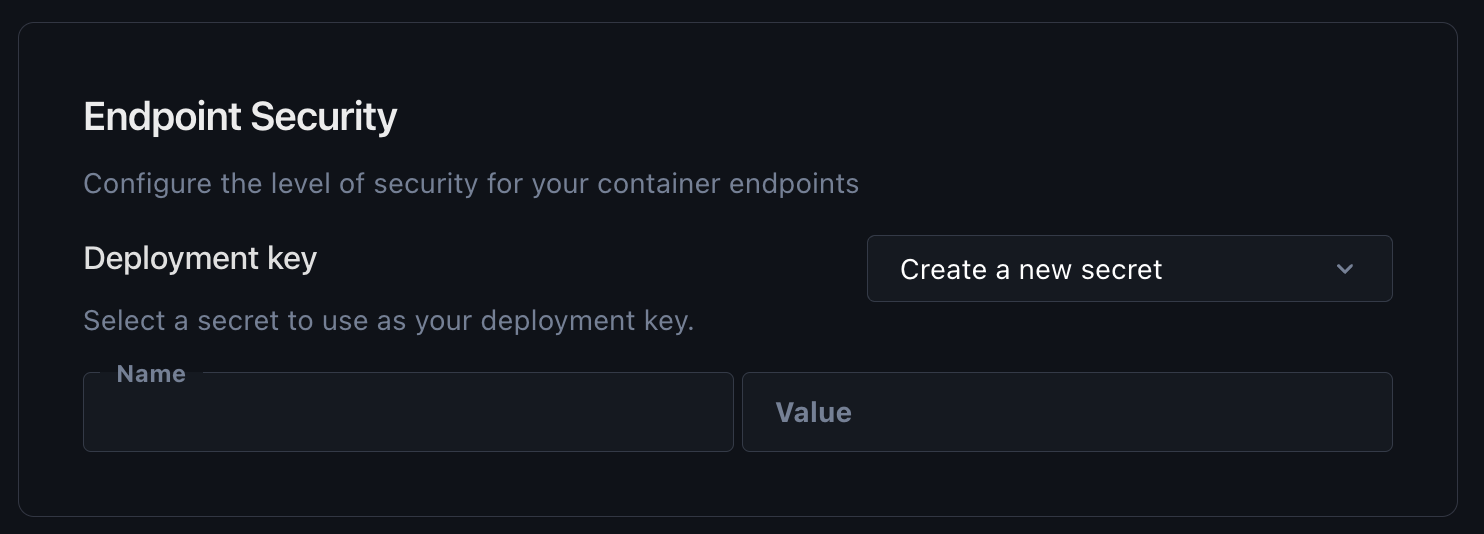
Once the deployment is set up with this configuration, the authentication token will not change unless there is a re-deploy, even if the underlying value for the Paperspace secret used to create the token is changed.
Authorization header usage
Once a protected endpoint is set up, the user will need two values to generate the authorization header: username and password.
The username for all Gradient deployments is paperspace. The password is the value of the secret specified during the deployment creation process.
To generate the authorization header value, the user will then need to encode username:password using basic access authentication. An example site to do the encoding can be found here.
As an example, if the password is "my_password", the user will encode "paperspace:my_password" using basic access authentication which returns Basic cGFwZXJzcGFjZTpteV9wYXNzd29yZA==.
The user can then pass that value in as through an authorization header like:
curl -H "Authorization: Basic cGFwZXJzcGFjZTpteV9wYXNzd29yZA==" https://abc123.paperspacegradient.com
The authentication token will only change on a redeploy of the deployment.
If a secret value was used to create the authorization, and then later changed while the deployment stays active, the security token will not change to that new value.
However, when the user redeploys, the authentication token will be updated to the current value of the Paperspace secret.